How to register Veeam Cloud Vault in Veeam Backup for Microsoft Azure
Article Applicability
This article documents a procedure for integrating Veeam Data Vault with Veeam Backup for Microsoft Azure.
This capability will be included natively in the next release of Veeam Backup for Microsoft Azure, and at that time, this article will then be retired.
Purpose
This article documents the procedure for registering Veeam Cloud Vault in Veeam Backup for Microsoft Azure.
Solution
Software Prerequisites
- Veeam Backup & Replication v12.3.1
- Veeam Backup for Microsoft Azure v8
Instructions
Part 1: Register Vault Repository
- Register the Veeam Cloud Vault repository in Veeam Backup & Replication.
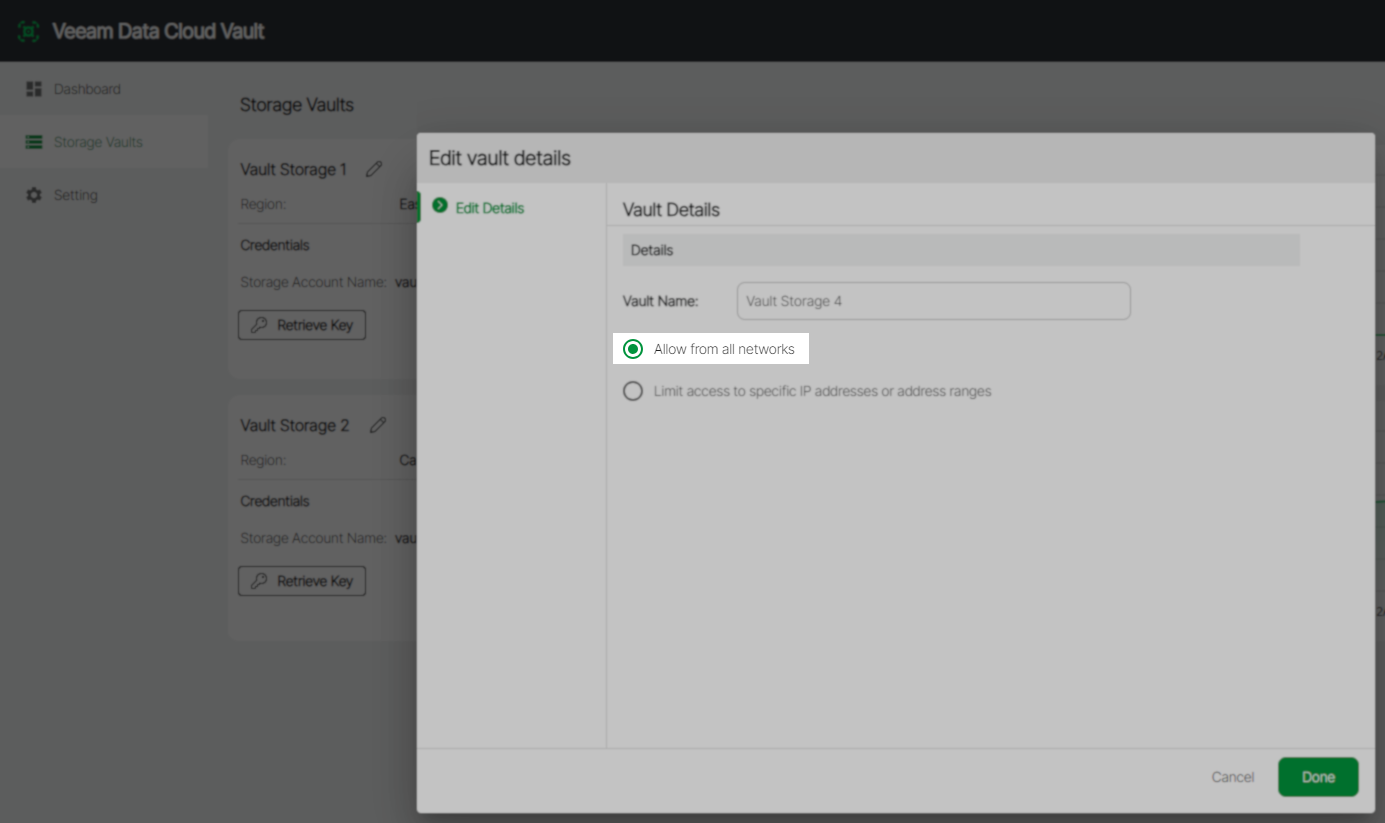
- After registering Veeam Cloud Vault using Veeam Backup & Replication, navigate to the VDC Portal and select the "Allow from all networks" option for the registered Vault.
Part 2: Extract Vault Connection Details from Configuration Database
Expand the section below based on which SQL Database engine is used to host the Veeam Backup & Replication configuration database.
Hint: To identify which database engine is in use, use the PowerShell script from KB1471.
Part 3: Extract the Certificate Data from the Encrypted Value
- Open Windows PowerShell ISE using the Run as administrator.
- Start a new script, if a new one is not automatically opened, and paste in the following script:
Do not run the script yet.
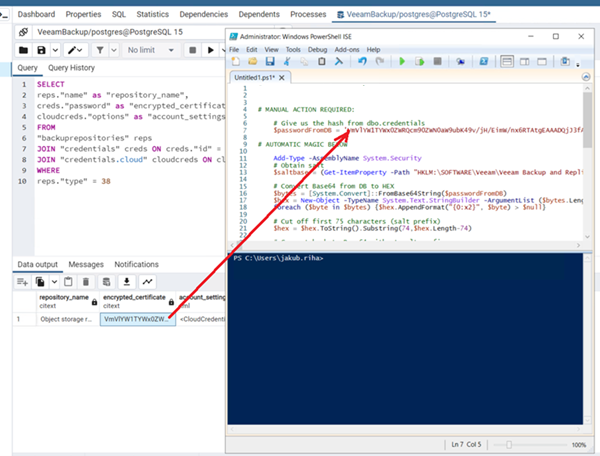
- On Line 4, replace the
INPUT_DATA_HEREplaceholder with theencrypted_certificatevalue copied from the configuration database in Step 7 (in Part 2).
.png?ck=1746631925649)
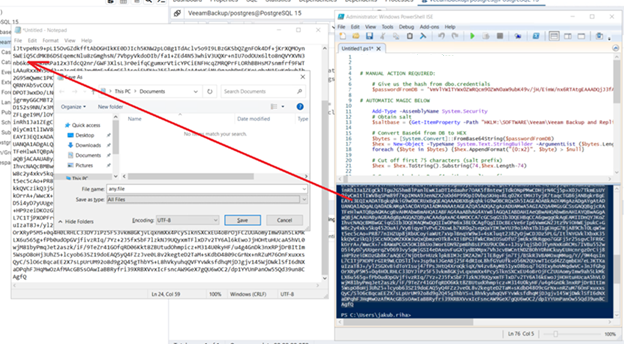
- Run the updated PowerShell script and save the output value of $chars to a file for use in the next steps.
Save the file with the extension .crt to make it easier to find in Step 13.
Part 4: Import the Certificate and Export PFX File
- Open the Certificate Manager (certmgr.msc).
- Expand the Personal node, right-click on Certificates, and select Import from the context menu under All Tasks.
- When prompted to specify the file to be imported, select the file created in Step 11.
Depending on the file extension of the file created in Step 11, you may have to change the file extension filter in the file Open browser. - On the Private key protection step, select the option Mark this key as exportable.
The password field can be left empty.
- When prompted to specify the file to be imported, select the file created in Step 11.
- After importing the certificate, right-click on the certificate and under All Tasks select Export.
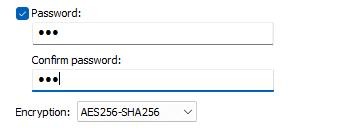
- Select the option for Yes, export the private key.
- Choose AES256-SHA256 as the encryption and specify a password that will later be used in Veeam Backup for Microsoft Azure.
- Save it as a PFX file.
Part 5: Add the Service Account to Veeam Backup for Microsoft Azure
- Log in to Veeam Backup for Microsoft Azure.
- Add a new Service Account.
- On the Type tab of the wizard, select Specify existing service account.
- On the Login tab of the wizard:
- Specify the Application ID and Tenant ID using the information within the account_settings value saved in Step 7 (in Part 2).
account_settings example:<CloudCredentialsOptions> <AzureStorageAccountOptions> <TenantId>4eff6498-b64e-4bc5-9443-fa212bfdddfg</TenantId> <EnvironmentType>0</EnvironmentType> <ApplicationId>cabb0705-3ec3-430a-8c6b-9835e6e72c61/ApplicationId> <RegistrationMode>2</RegistrationMode> <CertificateSerialNumber>2EB6C292C71FF4AA4CB53A71BDE9109E</CertificateSerialNumber> <CredentialsType>2</CredentialsType> <TenantLicenses/> </AzureStorageAccountOptions> </CloudCredentialsOptions> - Select the radio option for Certificate and provide the PFX file exported in Step 13.
- Specify the Application ID and Tenant ID using the information within the account_settings value saved in Step 7 (in Part 2).
- On the Roles tab of the wizard, toggle the Enable granular role assignment, then click the link to Edit Roles.
- Check only Repository management.
- Uncheck all Operational roles.
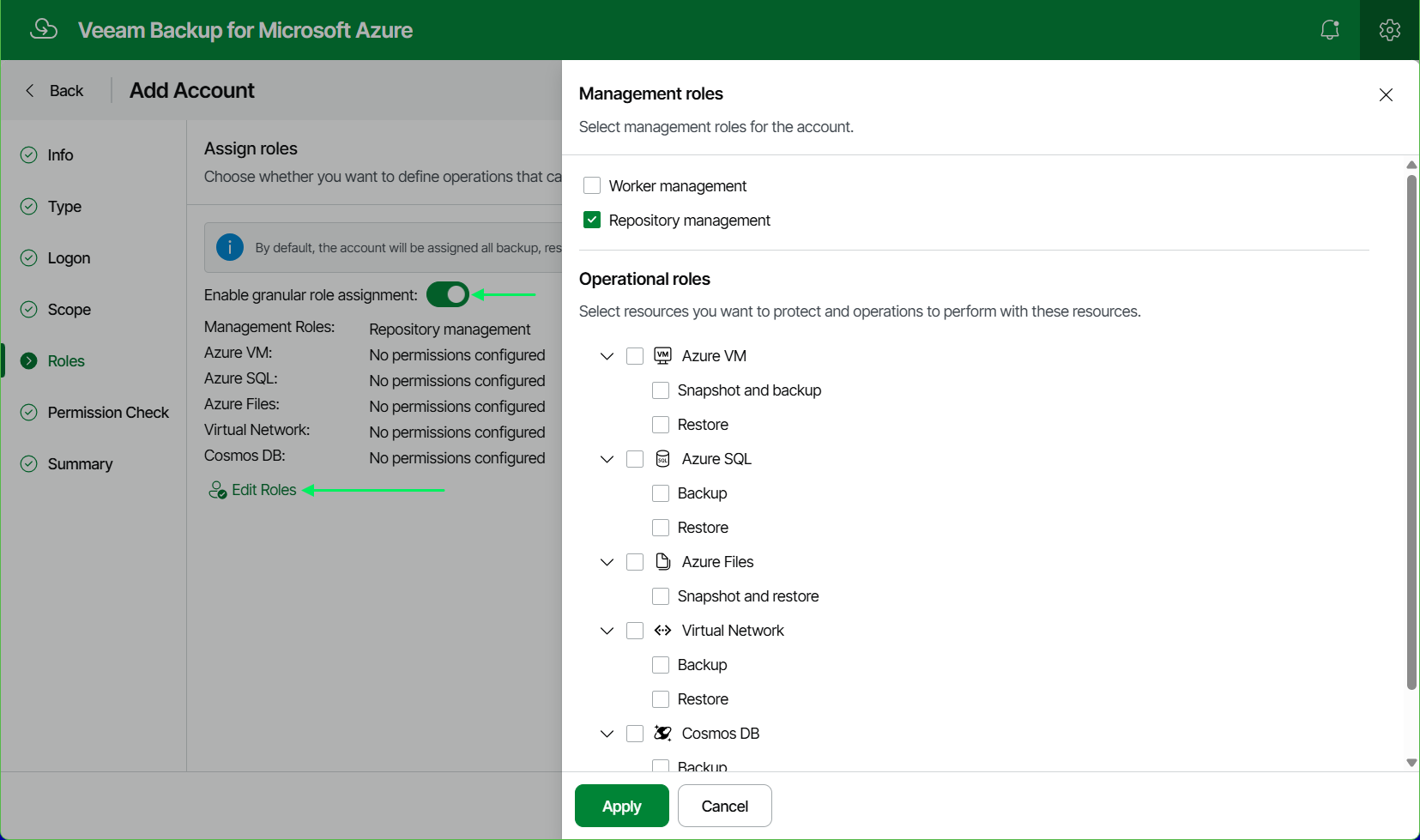
- Complete the Service Account creation wizard and use the newly registered Veeam Cloud Vault repository.
Note: The Permission check step of the wizard will fail with the error, "Your account is missing the required permissions." this is expected.
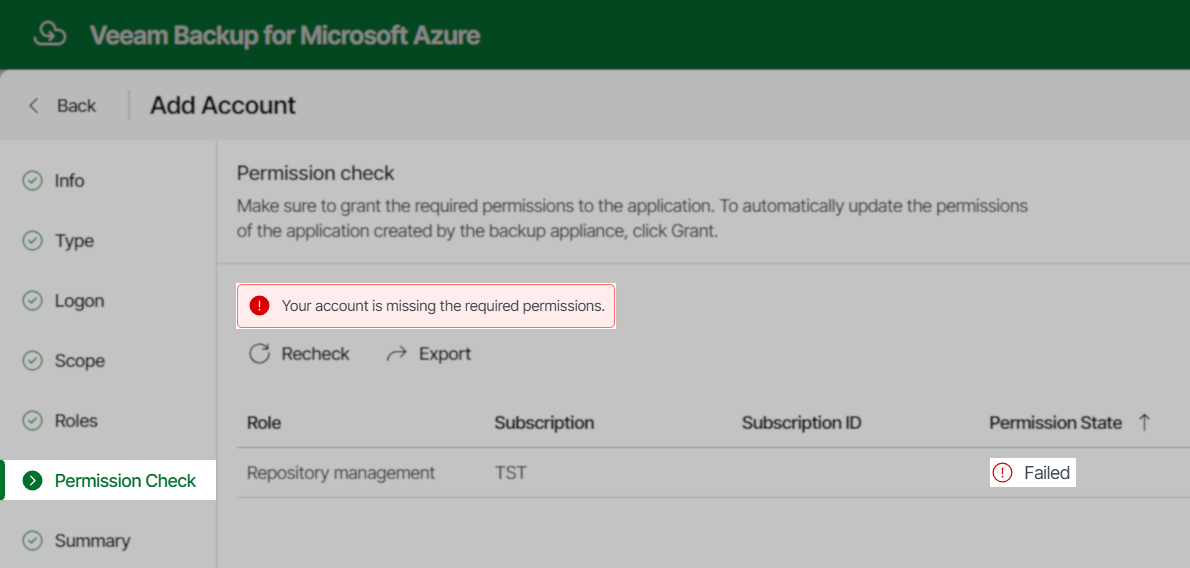
This is expected behavior and can be ignored.
To submit feedback regarding this article, please click this link: Send Article Feedback
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.

