Granular sudo Permissions for Management of Proxmox VE Host
Proxmox Virtualization Plug-in Version Requirement
The capability to add Proxmox VE to Veeam Backup & Replication using a non-root sudo user was added in Proxmox Virtual Environment Plug-In version 12.1.3.197 for Veeam Backup & Replication 12.3.
Purpose
This article provides an example granular ‘sudoers’ configuration for the Linux account that will be used by Veeam Backup & Replication when managing a Proxmox VE host.
Solution
Dedicated Proxmox Veeam User Creation
- Create an SSH login user.
Note: For the example permissions below, the account is namedveeamdep. Configure the sudoer permissions to match the user name you select. - Within the Proxmox configuration, add the user into the Datacenter.
Datacenter > Permissions > Users > Add - Add the Administrator role for the root path ( Path: / ) to that user.
Datacenter > Permissions > Add > User Permission
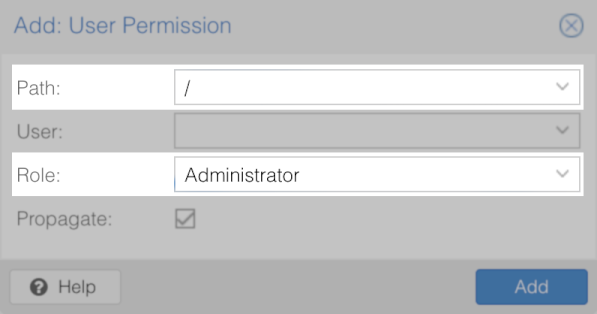
Proxmox Veeam User Account Specifications
- The Linux user account used by Veeam Backup & Replication for any Proxymox VE management operations must have /bin/bash shell set by default.
- The account must have root-equivalent permissions, which may be optionally restricted to the following specific list of commands as shown in the example sudoers file below:
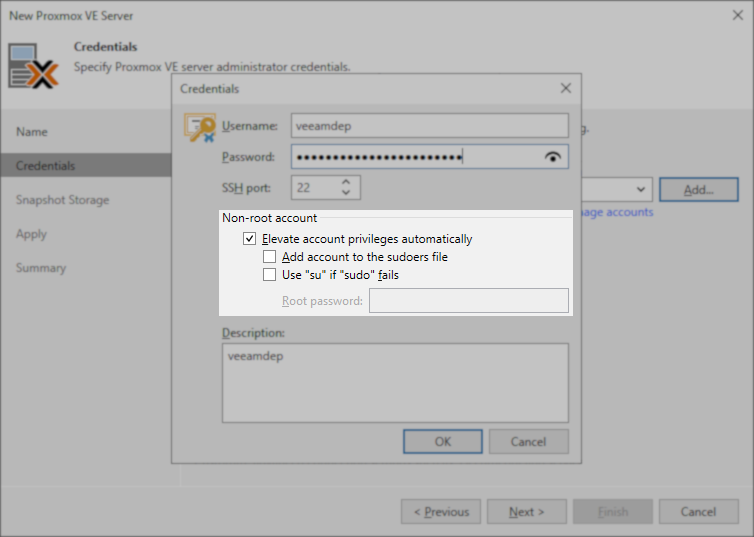
Credentials Configuration within Veeam Backup & Replication
Note: When using granular sudo permissions, ensure that the following options are not selected:
- Add account to the sudoers file — Enabling this option would cause the Veeam software to add the account to the sudoers file with broader permissions than those specified in the granular sudoers example.
- Use "su" if "sudo" fails — Enabling this option would cause Veeam Backup & Replication to switch to using the
rootaccount if any of thesudocommands fail due to a command not being included in the granular sudoers file. This could potentially mask a needed update to the granular sudoers file.
To submit feedback regarding this article, please click this link: Send Article Feedback
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.