How to Connect to an Object Storage Repository via Google Cloud Private Access
Purpose
This article documents how to configure Veeam Backup & Replication to use Google Cloud Private Access to connect to a GCS bucket instead of the public IPs for Scale-Out Backup Repository offload to Capacity Tier or Archive Tier or to connect to an Object Storage Repository in Veeam Backup & Replication 12 or newer.
Connectivity from on-premises to private access can be accomplished via Cloud VPN or Direct/Partner Interconnects to Google Cloud, and Private Access enabled on the VPC Subnet.
Note: Backup repository servers located in GCE need to be on a VPC Subnet where Private Access is enabled.
Solution
Prepare the Google Cloud Environment
- Make sure the VPC Subnet(s) that traffic will traverse have Private Google Access enabled:
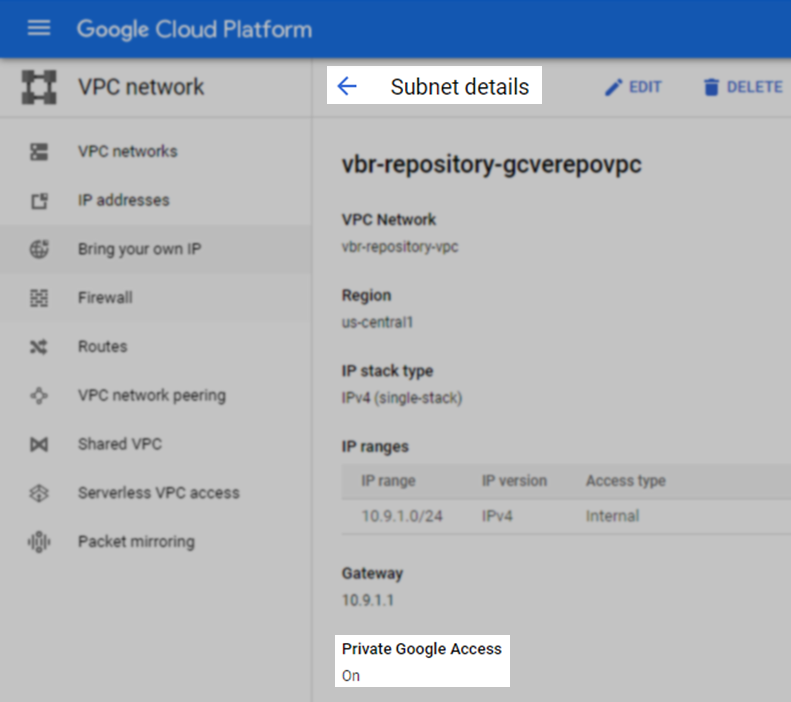
Prepare the On-Prem DNS
- Configure DNS servers used by repository servers to have a zone for googleapis.com.
- Create DNS A Records for private.googleapis.com pointing to 199.36.153.8, 199.36.153.9, 199.36.153.10, 199.36.153.11.
- Set up a CNAME record for *.googleapis.com to point to private.googleapis.com.
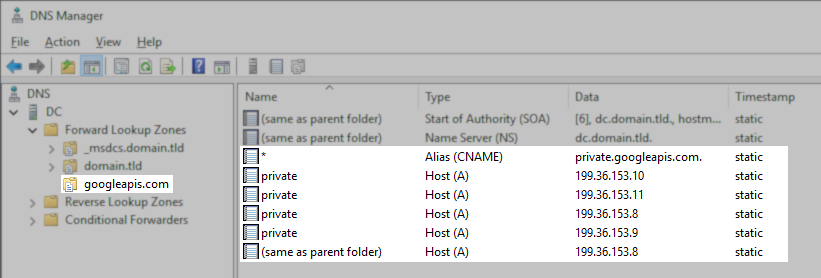
- For repository servers on-premises, ensure the CloudVPN or Cloud Interconnect uses dynamic routes or has a static route for the 199.36.153.8/30 pointing to the VPC subnet with Private Google Access enabled, and that the subnet is configured to send this traffic to the default internet gateway.
Prepare the Veeam Backup & Replication Environment
- To configure the Helper Appliance used for Object Storage Repository Health Checks to use the private IP address, add the following registry value on the Veeam Backup Server:
Key Location: HKLM\SOFTWARE\Veeam\Veeam Backup and Replication
Value Name: ArchiveUsePrivateIpForGoogleHelperAppliance
Value Type: DWORD (32-Bit) Value
Value Data: 1
1 = Enable Archive Appliance use Private IP | 0 = Disable (Default)
Add Object Storage Repository
Add the Google Cloud Oject Storage to Veeam Backup & Replication.
More Information
If the Gateway server assigned with the Object Storage Repository settings has a restricted internet connection, that machine cannot perform Certificate Renovation List (CRL) checks. In such a scenario, disable certificate revocation checks by creating the following setting on the machine assigned as the Gateway server within the Object Storage Repository settings.
Note: This setting will disable TLS revocation checks for all interactions with Object Storage performed by the machine where the registry value is created.
- For Windows-based Gateway servers, create the following registry value:
Key Location: HKLM\SOFTWARE\Veeam\Veeam Backup and Replication\
Value Name: ObjectStorageTlsRevocationCheck
Value Type: DWORD (32-Bit) Value
Value Data: 0 - For Linux-based Gateway servers, add the following entry to the /etc/VeeamAgentConfigIf the /etc/VeeamAgentConfig file is not present, it must be created. file:
ObjectStorageTlsRevocationCheck=0
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.