Windows Defender Application Control (WDAC) Supplemental Policy for Veeam Backup & Replication 12 Components Running on Azure Stack HCI 22H2
Challenge
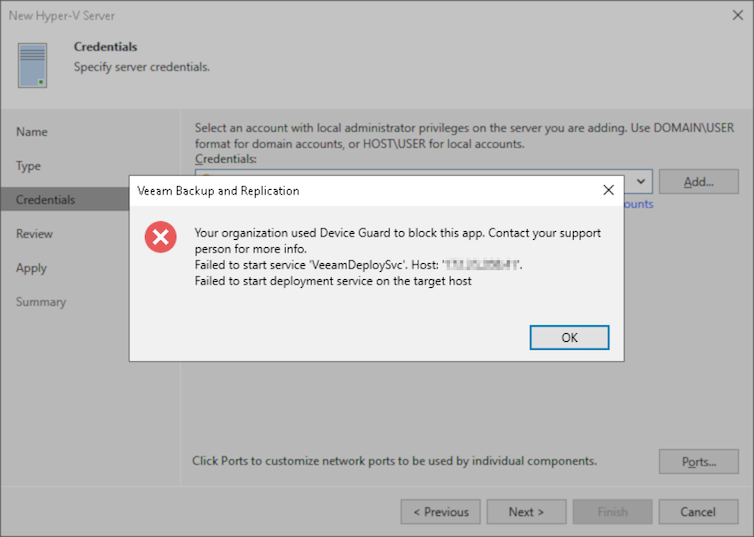
When attempting to add an Azure Stack HCI OS 22H2 cluster or node to Veeam Backup & Replication, the following error occurs:
Your organization used Device Guard to block this app. Contact your support person for more info. Failed to start service 'VeeamDeploySvc'. Host: 'x.x.x.x'. Failed to start deployment service on the target host
Cause
By default, the Azure Stack HCI OS 22H2 Supplemental Package has Windows Defender Application Control (WDAC) enabled and running in the enforcement mode. WDAC is a software-based security layer that reduces the attack surface by enforcing an explicit list of software that is allowed to run. WDAC limits the applications and the code that can run on the core platform.
To allow third-party non-Microsoft signed software to run on Azure Stack HCI nodes, a WDAC supplemental policy provided by the third-party software vendor must be installed.
Solution
Veeam Backup & Replication WDAC Supplemental Policy Deployment
The supplied XML policy is already linked to an Azure Stack HCI base WDAC policy {A6368F66-E2C9-4AA2-AB79-8743F6597683}
- Download the Policy XML Package from the Download Information section below.
- Execute the following command to Convert the XML policy to a binary format:
- Deploy the policy.
Policy files must have the nomenclature {PolicyID}.cip and are stored in C:\Windows\System32\CodeIntegrity\CiPolicies\Active\
The PolicyID is found within the source XML file. The PolicyID for the attached file is 48D8AD47-2B5F-4134-8C68-C320DC2D116A, so the policy file name must be named {48D8AD47-2B5F-4134-8C68-C320DC2D116A}.cip
Use the following command to copy the binary formatted policy to the destination:
- To activate the supplemental policy, either reboot the machine or invoke the code integrity policy refresher tool. The tool will try to activate all policies in the active policy folder:
Alternatively, you can use the RefreshPolicy.exe tool:
C:\wdac\RefreshPolicy.exe Rebootless ConfigCI Policy Refreshing Succeeded!
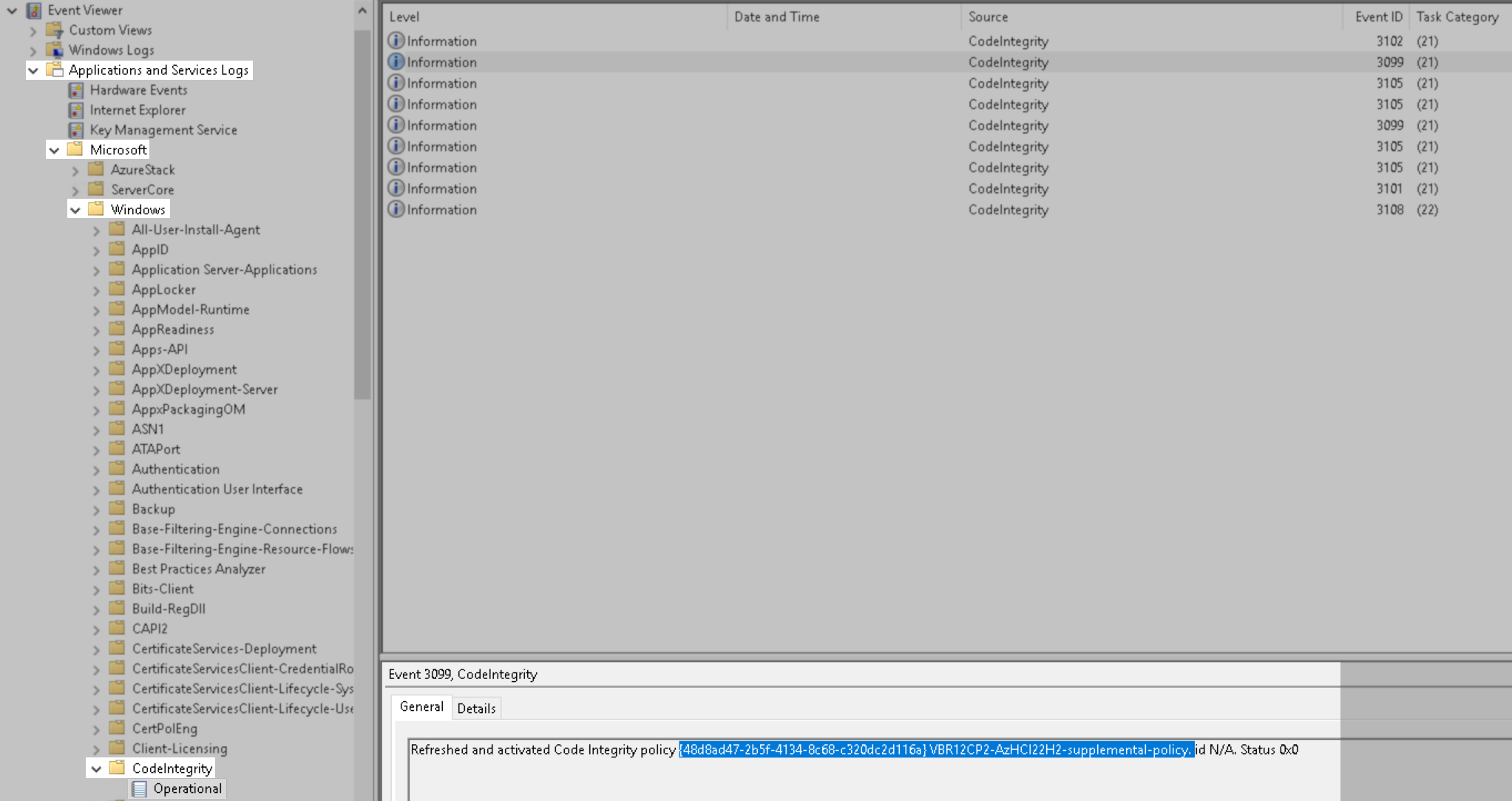
- Check Events in the Application and Services Logs > Microsoft > Windows > CodeIntegrity > Operational event log to determine if the policy has been activated:
Download Information
To report a typo on this page, highlight the typo with your mouse and press CTRL + Enter.